31 March 2020

At AWS re:Invent 2019, Amazon Detective was announced as a service to investigate and identify the root cause of potential security issues or suspicious activities. This week the service has become generally available.
Security services have been slowly increasing in the AWS landscape with VPC Flow Logs, Config, CloudTrail, GuardDuty, Security Hub and many other points of information to analyze during an investigation which can be tedious. Detective aims to help with that.
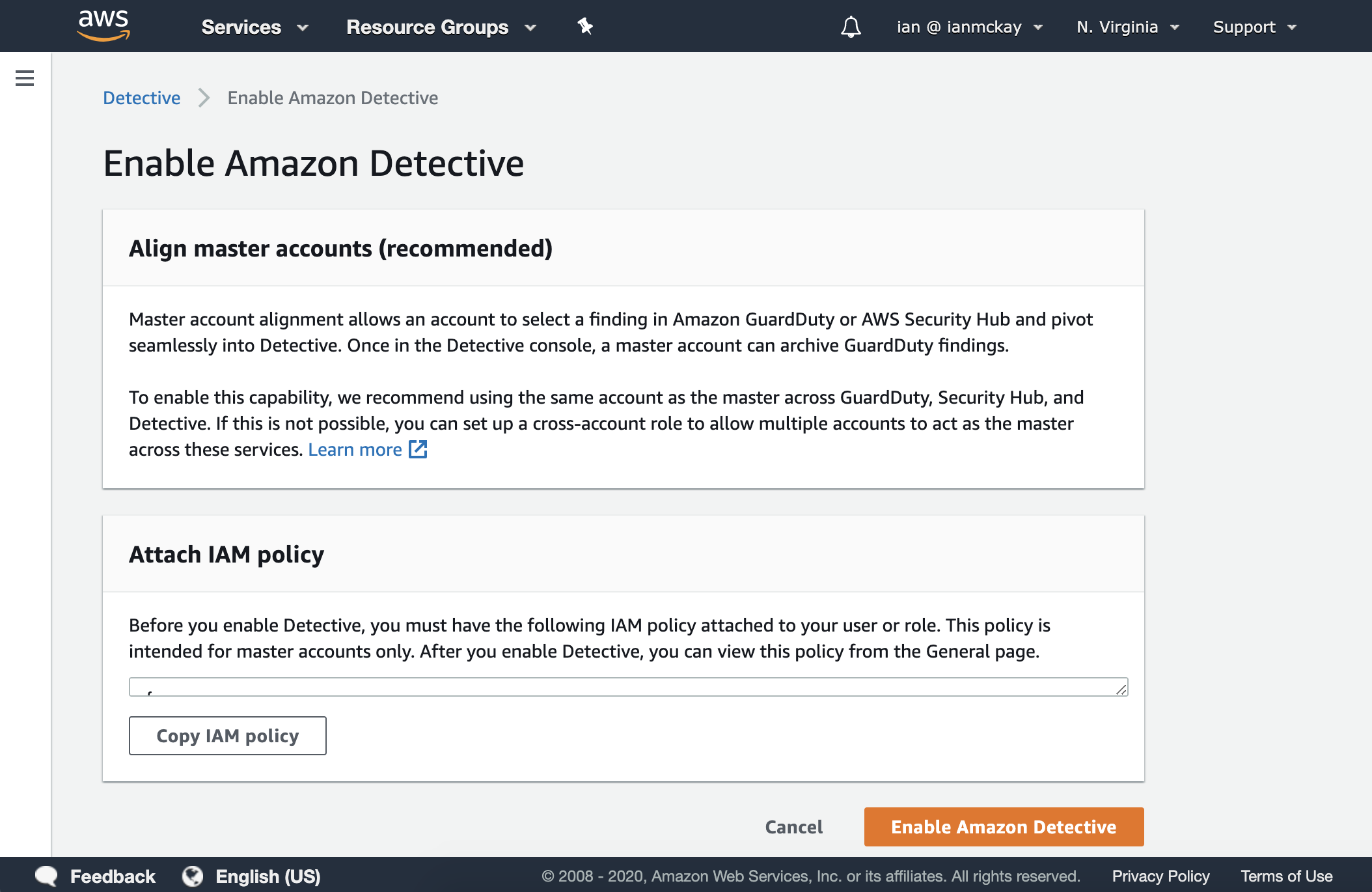
Enabling Detective works much like GuardDuty does, with a simple enable function and the ability to invite additional accounts to a master. Detective recommends you keep it, GuardDuty and Security Hub in the same account to allow for easy pivoting to occur.
When inviting a member account, you will be given the option to specify an e-mail address and personalized invitation message to the member account owner. Note that the principal who accepts the member account invitation must have the detective:AcceptInvitation IAM permission.
Once enabled, entity data will usually become available within 24 hours.
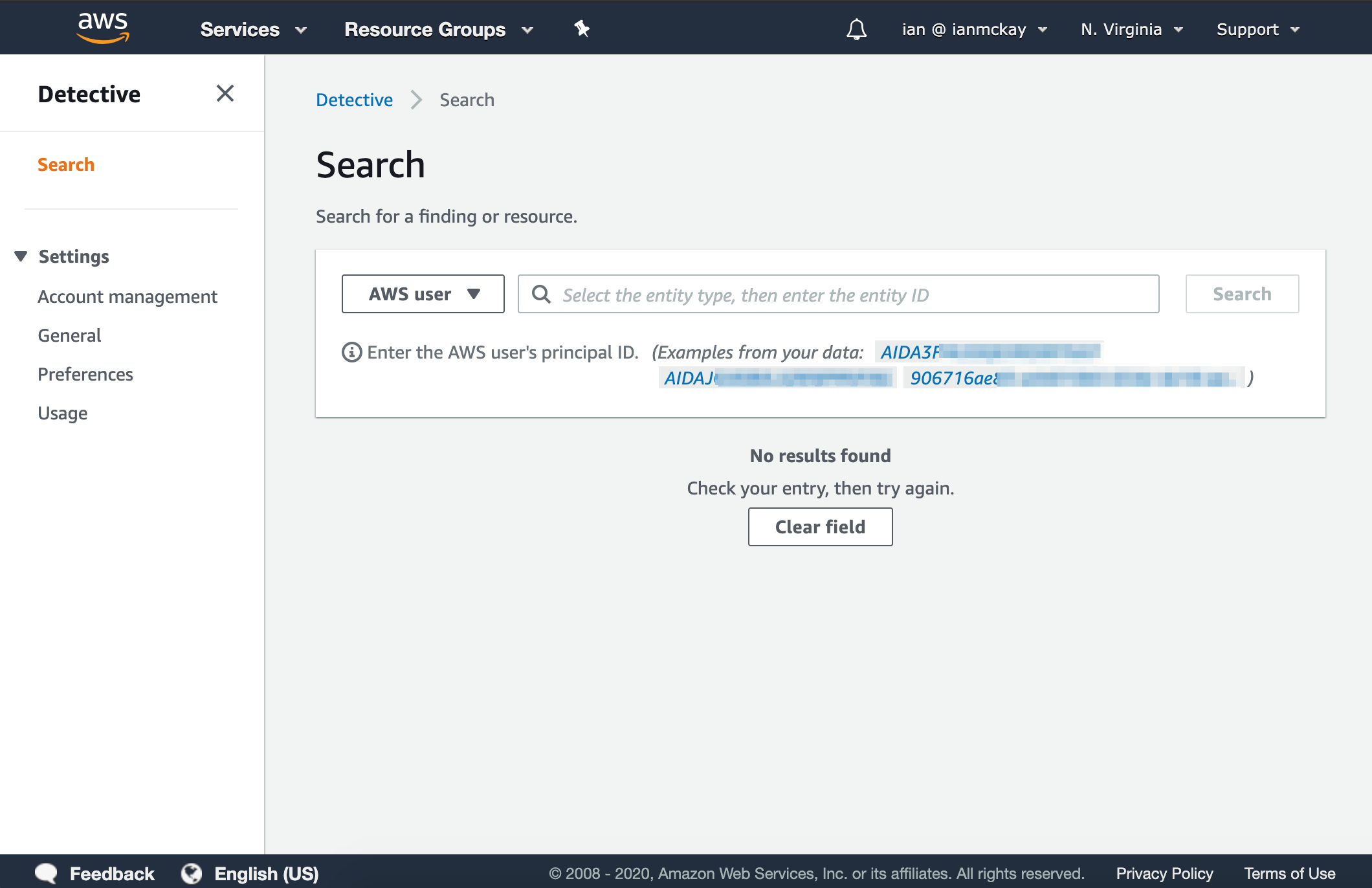
Once Detective has completed its backfill, you can use the search facility to look for supported entities to begin with. You should select a type from the dropdown box which will give you some suggestions for that type of entity.
Unfortunately, it seems as if the search box doesn’t actually perform any sort of search, but rather expects you to enter an identifier in whatever way the service expects. This means I often found myself switching back and forth between entity types to discover new entities via the suggestions list.
The following entities are supported at launch:
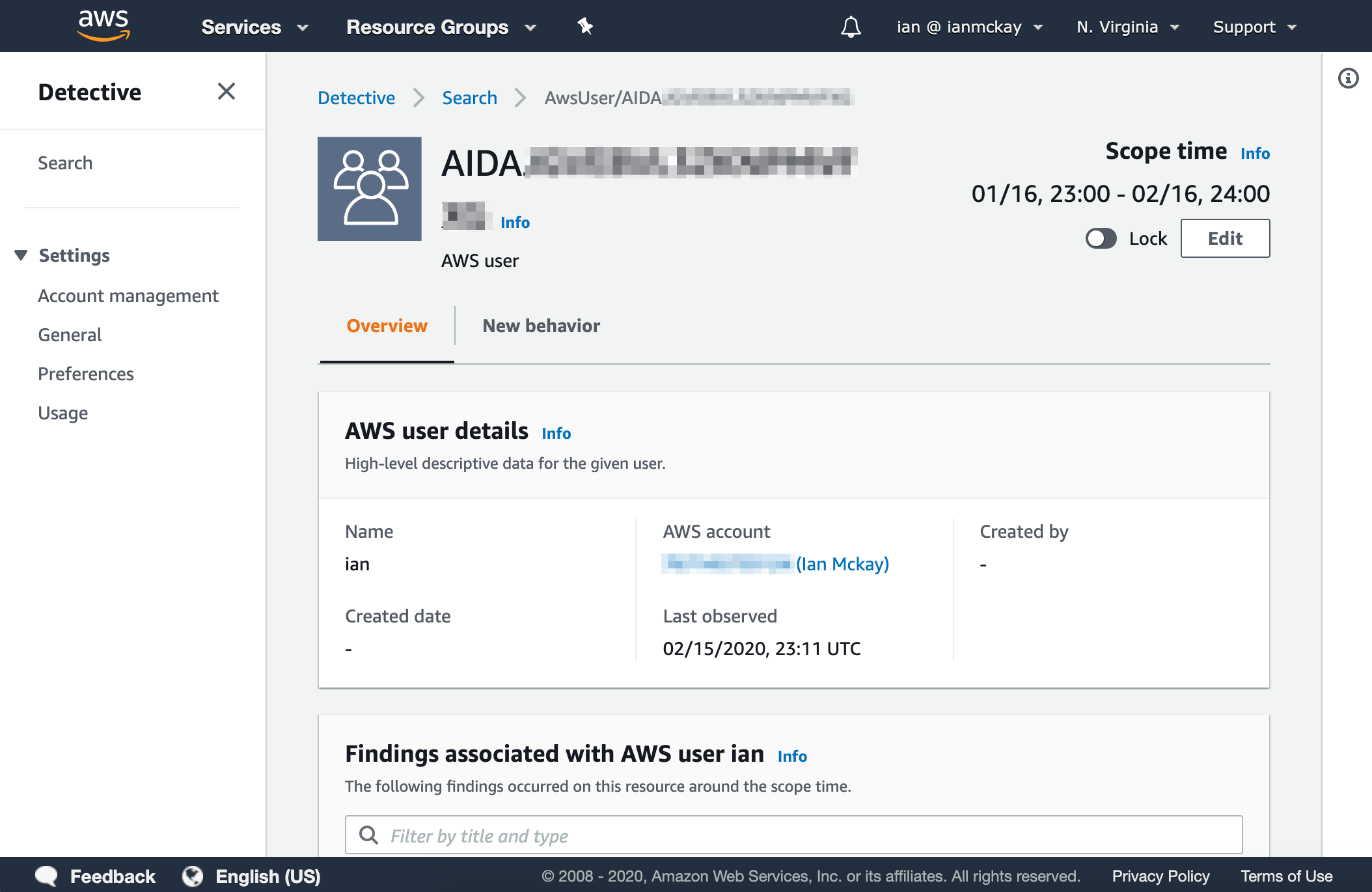
Looking at my IAM user, we see some general information about the user, a list of GuardDuty findings associated with the user and a graph of successful and failed API calls for the time period (known as the scope time) specified.
All graphs in Detective have the ability to switch between linear and logarithmic scale. This has the benefit of easily seeing both low frequency and high frequency calls within the same scope time.
Clicking through the graph brings up a table of API call counts by IP address, API method and access key which I can use to pivot.
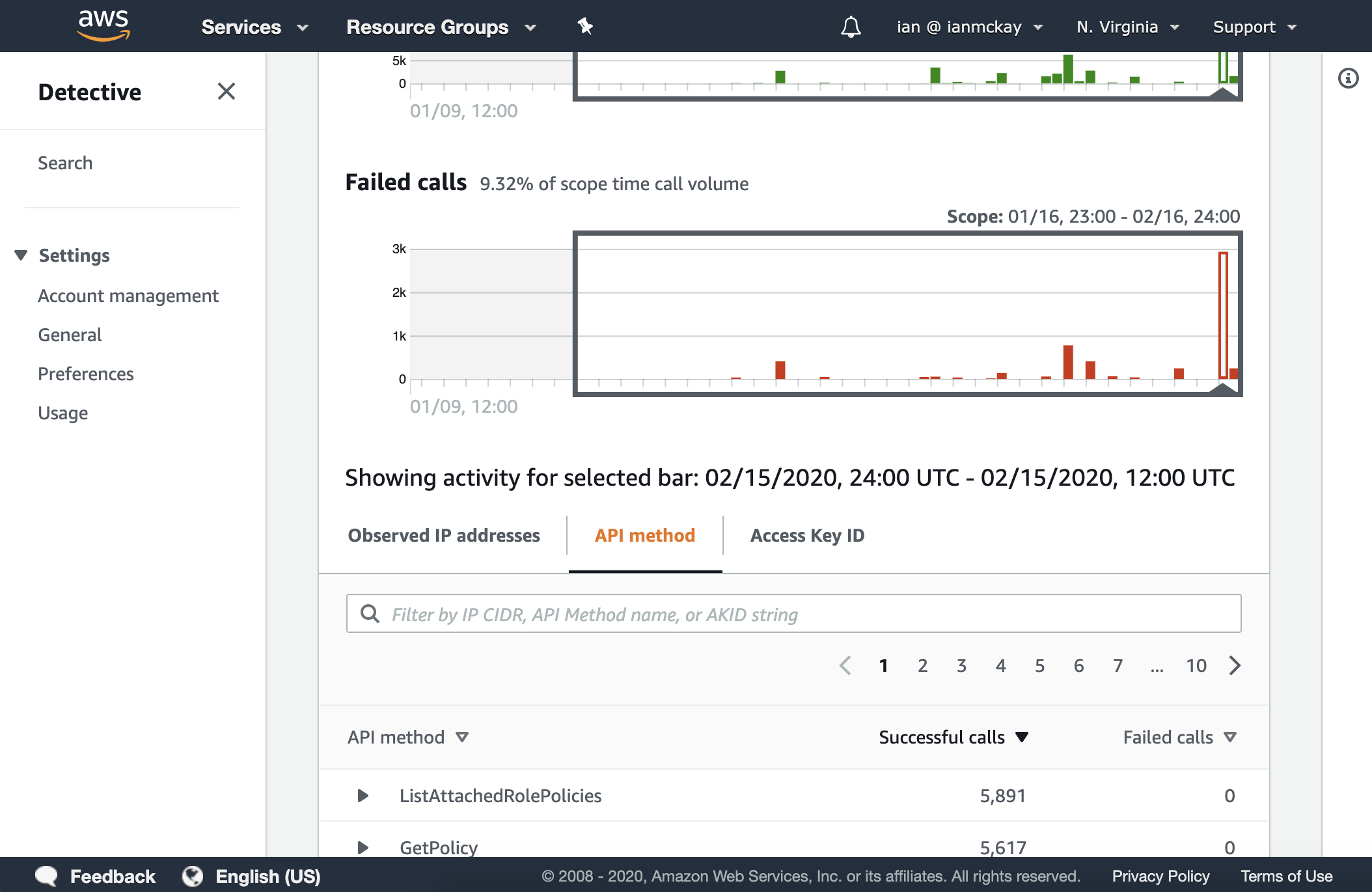
There are also other interesting panels within certain entities such as bar charts for VPC flows and geolocation charts to show IP or user agent usage across a map of the world.
Most tables and data points are linked in so you can easily pivot into other entity types. It’s important to note that the scope time can change when performing this action. If you prefer for this not to happen, there is a toggle to lock the scope time regardless of where you are.
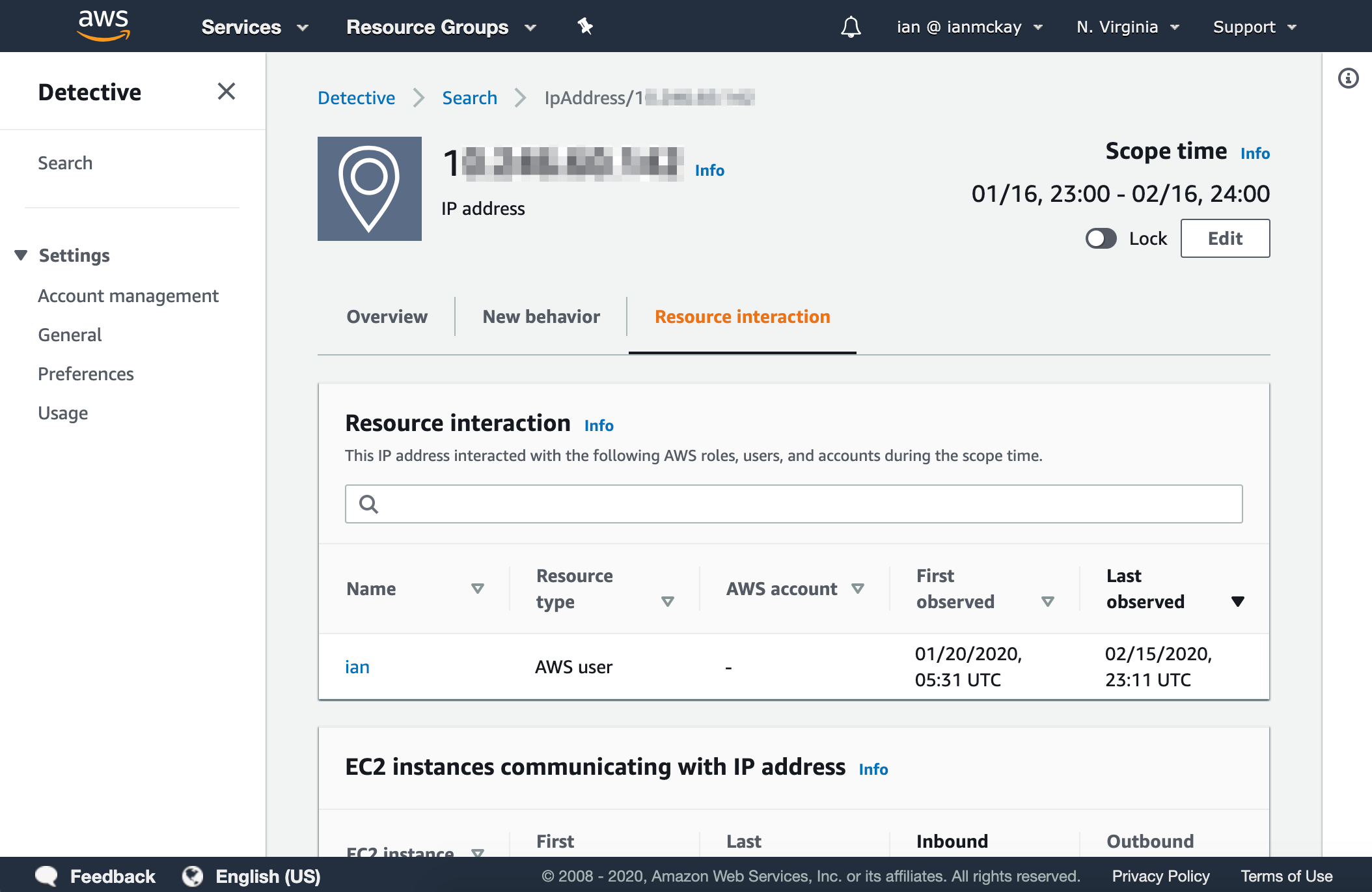
Entities may also have a resource interaction tab to show related entities as well as type-specific data points (for example, communicating EC2 instances for a specific IP address).
This ability to easily pivot between data points from various services is, in my opinion, one of Detective’s key features.
As with any new service, Detective isn’t perfect and has some things that may be improved as the service progresses past its initial release.
I believe that the previously mentioned lack of search is the most obvious limitation, however there are some additional rough edges I found:
securityhub.amazonaws.com can be confusing and pollute the searchAn additional issue I discovered during testing was that calls to S3 produce CloudTrail logs that wrap the user agent in an array, making calls look like [Mozilla/5.0]. This means that a distinct user agent entity is shown in Detective for these calls. Despite this being the only service that logs like this, the S3 service team confirmed this was working as intended and would not be changing their CloudTrail log format.
Analysis of data and storage of historical account data incurs no cost in Detective. Detective is only priced per GB of data ingested from its various sources.
Pricing begins at $2.00 USD per GB per month, which drops down to $0.25 USD per GB by the time you push over 10TB of data. A 30-day free trial is also available for you to try out the service.
At launch, Detective is available in 14 AWS commercial regions.
Amazon Detective is a powerful new service to make incident investigations easier to conduct with its data aggregation features. Though in its preliminary stages, it will likely become an essential part of a security teams toolset alongside Security Hub, GuardDuty and others.